Introduction
As the global shift to remote work continues into 2024, organizations must adopt robust cybersecurity strategies for remote work to safeguard sensitive data and maintain operational integrity. The rise of remote work has provided unprecedented flexibility for employees, but it also introduces new vulnerabilities. From unsecured home networks to increasingly sophisticated cyberattacks, organizations face a multitude of security challenges. In this environment, effective cybersecurity practices are essential for protecting both employees and the organization from data breaches, ransomware, phishing, and other digital threats.
In this article, we’ll explore advanced cybersecurity strategies for remote work that address emerging threats and empower organizations to build secure remote work environments.
The Growing Threat Landscape for Remote Work
Remote work has expanded the traditional corporate security perimeter, creating new opportunities for cybercriminals to exploit weaknesses. In 2024, cyber threats are more advanced and frequent than ever before, with hackers targeting remote employees using various methods such as phishing emails, malware attacks, and even vulnerabilities in commonly used remote work software.
Key areas of concern include:
- Unsecured Home Networks: Many remote workers rely on personal Wi-Fi networks that may lack the same level of security as corporate networks.
- Increased Use of Personal Devices: Employees often use personal devices to access sensitive company data, which can lead to security vulnerabilities if proper measures aren’t in place.
- Cloud Dependency: The growing reliance on cloud-based collaboration tools creates potential entry points for cyberattacks if not adequately protected.
These factors highlight the urgent need for organizations to adopt strong cybersecurity strategies for remote work to stay ahead of evolving threats.
Essential Cybersecurity Strategies for Remote Work in 2024
To ensure a secure remote work environment, organizations must focus on several key strategies designed to mitigate the risks associated with working outside the traditional office setting.
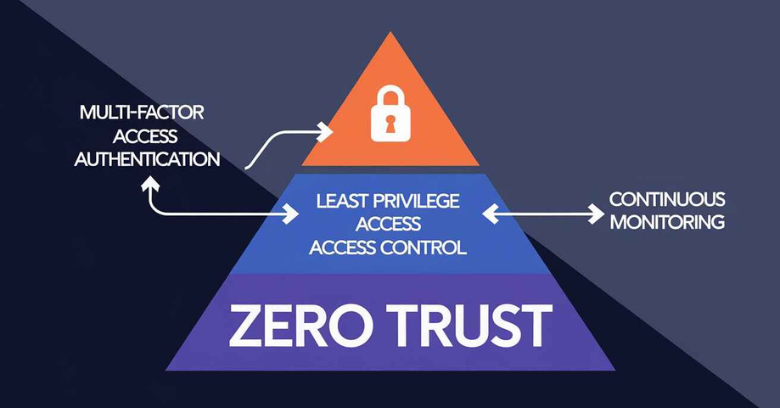
1. Implement Zero Trust Architecture
The Zero Trust model has become a cornerstone of modern cybersecurity strategies, especially in remote work environments. Rather than assuming trust for users and devices inside the network, Zero Trust enforces strict identity verification for every individual and device attempting to access resources, regardless of their location.
Key Elements of Zero Trust:
- Multi-Factor Authentication (MFA): Require multiple forms of authentication (e.g., passwords and biometrics) to ensure that users are who they claim to be.
- Least Privilege Access: Only grant employees the minimum level of access needed to perform their job functions, reducing the potential attack surface.
- Continuous Monitoring: Continuously monitor network traffic and user behavior to detect and respond to suspicious activities in real-time.
2. Strengthen Endpoint Security
With remote employees using a variety of devices to access corporate data, endpoint security is more critical than ever. Endpoint protection ensures that all devices, including laptops, tablets, and smartphones, are secured against threats, regardless of where they are being used.
Best Practices for Endpoint Security:
- Install Endpoint Detection and Response (EDR) Solutions: EDR tools actively monitor and respond to threats at the device level, providing real-time protection and alerting security teams to potential breaches.
- Ensure Regular Updates and Patching: Devices used for remote work must always have the latest security updates and patches applied to avoid vulnerabilities that hackers can exploit.
- Encrypt Sensitive Data: Ensure that all sensitive data on remote devices is encrypted to prevent unauthorized access in the event of device loss or theft.
3. Secure Cloud Collaboration Tools
As remote teams increasingly rely on cloud-based tools for communication and collaboration, securing these platforms is essential. While cloud services provide flexibility, they can also expose sensitive information if not properly secured.
Cloud Security Strategies:
- Use Strong Access Controls: Limit access to cloud tools based on user roles and responsibilities, ensuring that only authorized individuals can view and modify sensitive data.
- Data Encryption: Encrypt all data stored and transmitted via cloud services to protect it from unauthorized access during transit.
- Regular Audits: Conduct regular security audits of cloud services to ensure compliance with security policies and to identify potential vulnerabilities.
4. Develop a Comprehensive Security Awareness Program
Human error remains one of the biggest cybersecurity risks, especially in remote work environments. A well-developed security awareness program can help employees recognize and respond appropriately to threats like phishing, social engineering, and ransomware attacks.
Components of an Effective Security Awareness Program:
- Regular Training: Offer mandatory cybersecurity training sessions to educate employees on recognizing threats and following best practices for data protection.
- Phishing Simulations: Run simulated phishing campaigns to test employee responses and provide additional training to those who fall for these tests.
- Clear Communication Channels: Establish clear channels for reporting suspicious activities, ensuring that employees can quickly alert the IT team when they encounter potential threats.

5. Implement Multi-Factor Authentication (MFA)
One of the simplest yet most effective strategies to secure remote work environments is the use of Multi-Factor Authentication (MFA). MFA adds an extra layer of security by requiring users to verify their identity using at least two different forms of authentication, such as a password and a biometric factor (fingerprint, face scan, etc.).
Why MFA is Crucial for Remote Work:
- Reduces Risk of Credential Theft: Even if a hacker gains access to an employee’s password, they would still need a second factor to log in.
- Protects Against Phishing Attacks: MFA makes it harder for attackers to gain unauthorized access, even if they successfully trick an employee into providing login credentials.
Many organizations combine MFA with a Zero Trust architecture to further strengthen security in remote environments.
6. Use a Virtual Private Network (VPN)
Virtual Private Networks (VPNs) are essential for ensuring secure connections when remote workers access corporate networks from home or public Wi-Fi. A VPN encrypts the internet connection, making it difficult for hackers to intercept data.
Benefits of Using VPNs:
- Data Encryption: VPNs encrypt all data transmitted between the user’s device and the company’s network, ensuring that sensitive information remains secure.
- Secure Remote Access: VPNs allow employees to access company resources securely, even from untrusted networks like public Wi-Fi.
- Bypassing Geo-Restrictions: VPNs can allow employees to bypass geographic restrictions when accessing company data from different locations.
7. Implement Data Loss Prevention (DLP) Solutions
Remote work increases the risk of accidental data leaks or intentional data theft, especially when employees use personal devices or work in unsecured environments. Data Loss Prevention (DLP) solutions help prevent sensitive data from being shared or transferred outside of approved channels.
How DLP Solutions Work:
- Monitor Data Movement: DLP tools track how data is accessed, used, and transmitted across devices and networks, preventing unauthorized sharing of sensitive information.
- Block Unapproved Transfers: DLP systems can automatically block the transfer of sensitive files via email, messaging apps, or external storage devices if they don’t meet pre-approved criteria.
- Alert Security Teams: If suspicious activity is detected, DLP solutions can alert the security team for further investigation.
Emerging Threats in Remote Work Cybersecurity
In 2024, remote work security strategies must also address new and emerging threats that specifically target decentralized and remote work environments.
1. Ransomware-as-a-Service (RaaS)
Ransomware continues to be one of the most significant cybersecurity threats, and Ransomware-as-a-Service (RaaS) is making it easier for cybercriminals to launch ransomware attacks. With RaaS, attackers can rent ready-made ransomware tools, allowing even those with limited technical expertise to execute attacks.
Preventive Measures:
- Regularly back up critical data to an isolated location.
- Implement robust endpoint security measures and anti-ransomware tools.
- Train employees to recognize phishing attacks that often lead to ransomware infections.
2. Deepfake and AI-Powered Attacks
As AI technology advances, deepfake and AI-powered attacks are becoming more sophisticated. These attacks use machine learning to generate convincing fake audio, video, or messages, tricking employees into transferring funds or sharing sensitive information.
How to Counter Deepfake Attacks:
- Use AI-powered detection tools to identify and flag deepfakes.
- Encourage employees to verify sensitive requests through multiple communication channels before taking action.
- Implement advanced fraud detection systems that leverage AI and behavioral analytics.
3. Supply Chain Attacks
Supply chain attacks occur when cybercriminals target third-party vendors or service providers to gain access to an organization’s network. In remote work environments, where reliance on third-party cloud services and software is common, supply chain attacks are a growing concern.
Mitigating Supply Chain Risks:
- Conduct thorough security assessments of third-party vendors before integrating their services.
- Implement continuous monitoring of vendor relationships to detect any suspicious activities.
- Use secure APIs and encryption to protect data exchanges between your organization and external partners.
Conclusion
In 2024, securing remote work environments requires a proactive, multi-layered approach. By implementing advanced cybersecurity strategies for remote work, organizations can effectively protect their remote workforce against a growing range of cyber threats. From adopting a Zero Trust architecture to strengthening endpoint security and educating employees on the latest phishing tactics, these strategies are essential for safeguarding sensitive data and maintaining operational resilience.
As remote work becomes increasingly common, staying ahead of emerging threats and continuously updating cybersecurity practices will be key to ensuring long-term security and success.